Publisher description
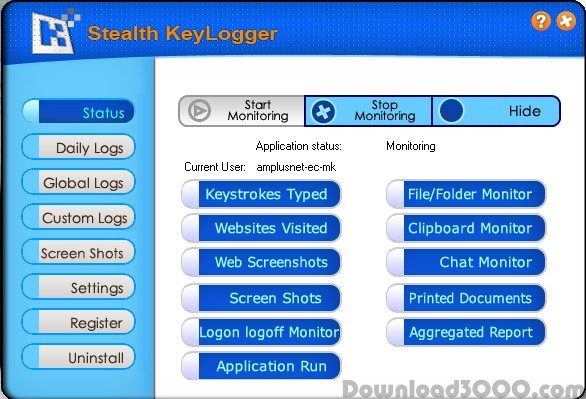
Stealth KeyLogger is an invisible, easy to use surveillance application, designed to monitor and record all activities on a computer. Perfectly suited for both office and home use Stealth KeyLogger offers detailed information on who uses your computer, their e-mails and chat conversations, the visited web sites, programs run as well as actual screenshots of their activity, websites visited and keystrokes history.You can schedule the exact period when you want that Stealth KeyLogger to monitor or, you can choose to exclude users from monitoring, and to specify when should the application record an user as being IDLE. On the other side there are new functionalities improved from the previous ones for a better surveillance in a better stealthy way. This keylogger keeps up with the technology progress, so that the version of Internet Browsers and Instant Messaging applications does not influence the results of the application. Reports are organized chronologically, always providing information on user, application and content (keystrokes, websites etc) and presented in a easy to read web format. For security reasons, reports may be printed or sent to a specified e-mail address. The improved email reporting gives you the liberty to choose which type of report you want to be send on e-mail, making the surveillance easier. You can also sent logs via Ftp, or save them to LAN. Stealth Keylogger can delete the old logs if the size specified is exceded. Stealth KeyLogger has a hotkey and password activation protection and runs in stealth mode being undetectable in Task Manager (applications and processes). To save disk space, the program can clear logs periodically or after sending them to you.
Related Programs

Keystrokes Logger Software 3.0.1.5
Keystrokes logger software monitors computer

Invisible Keylogger Software 3.0.1.5
Keylogger application captures keystrokes.

Stealth Chat Monitor, surveilance application

Hogense monitor keylogger is the best choice.

Computer Monitor Keylogger 4.9
Secretly monitor activity on your computer